Searching Steganography
By @5w0rdfish
If you are not sure what it is or how it is done head over to my blog post about it, Steganography 101
Some uses of Steganography:
• Privacy
• Freedom of Speech
• Whistleblowers
• Data Exfiltration
• Terrorist Communications
• Espionage
• Child Pornography
Metrics
I took a look back in 2015 into the search history of the search term "Steganography".
Although much more investigation could be achieved into the metrics of steganography and its popularity, I currently only have the time to update this blog post to see if any differences have occurred in the last three years. The metrics would be an interesting area of exploration for future research. I have updated some of the graph data where possible to reflect recent changes for 2018.
In 2001 it was an extremely popular term due to the public, and academics assuming of it use within the 9/11 attacks. With this, there began some investigation into its use within the public domain. Since then there has been a steady decline in the search metrics, which seems to have continued to this date.
However below shows the peaks that were seen during two periods of high activity, during this time the traffic for searching the term steganography nearly doubled in popularity. The increased traffic being within the month of September and October 2014. The first peak shows a rise in searches resulting from India, the second was found to be attributed to USA. It is believe geo-political events can impact possibly its search metric, however after some research on what was happening around this time, I think one of the peaks could be attributed to the general publics interest, as steganography appeared on a mainstream program in the USA :)
Although much more investigation could be achieved into the metrics of steganography and its popularity, I currently only have the time to update this blog post to see if any differences have occurred in the last three years. The metrics would be an interesting area of exploration for future research. I have updated some of the graph data where possible to reflect recent changes for 2018.
In 2001 it was an extremely popular term due to the public, and academics assuming of it use within the 9/11 attacks. With this, there began some investigation into its use within the public domain. Since then there has been a steady decline in the search metrics, which seems to have continued to this date.
However below shows the peaks that were seen during two periods of high activity, during this time the traffic for searching the term steganography nearly doubled in popularity. The increased traffic being within the month of September and October 2014. The first peak shows a rise in searches resulting from India, the second was found to be attributed to USA. It is believe geo-political events can impact possibly its search metric, however after some research on what was happening around this time, I think one of the peaks could be attributed to the general publics interest, as steganography appeared on a mainstream program in the USA :)
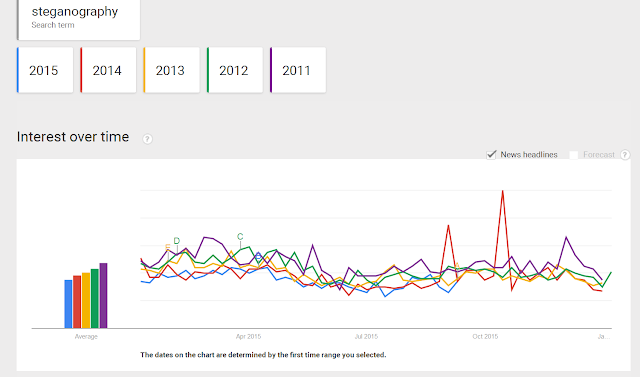
Interest over time - research undertaken 2015
In 2015 the countries that showed a prominent interest into the area of steganography are India, Iran, USA and the UK.
However now when reviewing the past five years data, things have changed somewhat with Googles data. As we can see India is still top of the list but other regions have taken over. We can clearly see the two spikes from 2014 which are really prominent now we have a longer data time line to look against, it would be good to dig deeper to see what may have caused these spikes further and get clarification on this.
Interest over time - research undertaken 2018
Steganography vs Cryptography
In 2014 - 2015 Cryptography on average was a much more popular search term in comparison to steganography, understandably. Surprisingly though, mobile searches for steganography were present for such a niche area of interest. We can see during one of the spikes, that the search amount for steganography was for 49k during the month of October.
Cryptography vs Steganography - research undertaken 2015
We can see since 2015, Cryptography has still remained popular, with Steganography maintaining its popularity, if not a slight decline. When introducing the term cryptography we can see Jordan and Indonesia coming into the mix into the country listing.
Cryptography vs Steganography - research undertaken 2018
Google now provides the ability to see search terms used on YouTube. Below shows this data, which looks much more volatile than the general website search. Which shows a peak with cryptography around the start of 2017. Also other countries seem to come onto the top ten list. However within Indonesia cryptography and steganography appears to be of a strong interest.
Cryptography vs Steganography - research undertaken 2018 - Youtube
Cryptography and Steganography are quite specialist fields to be searching for. With this is mind a generalist search term was used and “how to hide files” was looked into. This was trying to replicate more layman terms, possibly used by general users.
"How to hide files" search term - research undertaken 2015
It appears that "how to hide files" is starting to decline now also, however it has had a few peaks. Once again the country listing has changed. I also noted that there were operating system specific searches such as "how to hide files on android" and "how to hide files windows 8"recommended for data searches.
"How to hide files" search term - research undertaken 2018
I literally could spend all night drilling down into data and search terms to break these down further and see if any interesting research comes from it. Its more to give you the idea yourself to possibly look into these things for yourself. If you would like to and find anything of interest please do let me know. Take a look on Google Trends for yourself !
Use Cases
Steganography, similar to many modern day technologies can be used nefariously; however there are legitimate uses. For example, reporters looking to privately publish their works. This is especially important where the location of the reporter means that communications maybe blocked or monitored. They require the facility to disguise their communications in order to get the news to the masses.
“Twenty-one of the 25 top news organizations globally are targeted by state actors, said Morgan Marquis-Boire, director for security at First Look Media. Major media outlets continue to set aside insufficient budgets, if any, to protect their information, he added, and as a result, the onus falls to the reporter to educate and protect themselves” (Ekwo 2015).
 “A Pew Research Center study, surveying 2,723 practicing journalists and evaluating the 671 respondents showed half of the journalists working for a news organization (88 percent of respondents) said their organization is not doing enough to protect them and their sources. The same study found 71 percent of journalists had little or no confidence that ISPs could protect their data, and only two percent had a lot of confidence.” (Ekwo 2015)
“A Pew Research Center study, surveying 2,723 practicing journalists and evaluating the 671 respondents showed half of the journalists working for a news organization (88 percent of respondents) said their organization is not doing enough to protect them and their sources. The same study found 71 percent of journalists had little or no confidence that ISPs could protect their data, and only two percent had a lot of confidence.” (Ekwo 2015)
The Guardian newspaper provides the facility of “Secure Drop”, which provides a Tor backed encryption facility to assist with anonymity. It is suggested that steganography is used as part of this process.
The open source tool Camera/Shy created by international hacker group Hacktivismo provides a method of communication for activists operating behind national firewalls or alternatively those who are under oppressive regimes in order to overcome Internet censorship. They had released this tool with the intention of assisting Chinese dissidents communicate. Hactivismo has over thirty associates from North America, Europe, Russia, Israel, Australia, Taiwan, and Korea.
Terrorism
Terrorist factions such as Al-Qaeda, Hamas and Hezbollah are some that have been suspected of the use of steganography. Using steganography to embed maps and communication to their followers.
Reports previously have been in the news detailing how terrorists have communicated using videos as a cover file.
Computer forensic experts from the German Federal Criminal Police (BKA) discovered a pornographic video file name “kick-ass.mov”, when they arrested a suspected Al-Qaeda member in Berlin, 2011. They had found over 100 files detailing operations and plans within this video; such as “Lessons Learned”, “Report on Operations” and “Future works”. Fortunately for them it was not encrypted. This could have been uploaded to one of the 4.2 + million possible pornographic sites on the internet . Thus making the carrier files extremely accessible to those who know where to look, and a needle in the haystack operation for others.
Computer forensic experts from the German Federal Criminal Police (BKA) discovered a pornographic video file name “kick-ass.mov”, when they arrested a suspected Al-Qaeda member in Berlin, 2011. They had found over 100 files detailing operations and plans within this video; such as “Lessons Learned”, “Report on Operations” and “Future works”. Fortunately for them it was not encrypted. This could have been uploaded to one of the 4.2 + million possible pornographic sites on the internet . Thus making the carrier files extremely accessible to those who know where to look, and a needle in the haystack operation for others.
With extremists now becoming more technologically proficient, covert data is no longer reserved for espionage cases. It is felt since encryption and monitoring has become a focus of attention, that steganographic practices may become more mainstream to those who wish to preserve privacy or thwart attempts of detection. (Gallagher 2012)
Data Exfiltration
It is imperative that detection of such nefarious uses advances, not just for terrorist prevention but to also protect data. Data exfiltration is another result from using steganographic processes. Tripwire had released a recent report detailing that a fortune 500 company had become victim to a campaign.
The ongoing attack; where data had bypassed firewalls and Intrusion detection systems had used video based steganography. The videos which were all the same, all carried different parts of sensitive data out of the company via a video upload site. It was this duplication which led to the alert and detection. (Westin 2014)
It is not a new occurrence of steganography being used for a data exfiltration. It is not just for the exfiltration of data it has been used either; it has been used in the past to help facilitate that act obfuscating the transmission and communication to command and control centers of attackers. There are some notable Advance Persistent Threats that have used steganography with this method to carry out malicious campaigns.
Some other malware variants that have been found are and can be read about in the Trendmicro Steganography malware series (Sancho 2015) are :ZeusVM: hiding malware configuration inside JPG images, VAWTRAK hides configuration file in a remote favicon image file, FakeReg hides malware settings in the app icon. However it isn’t just images that are being used an example is VBKlip hides data within the HTTP protocol targeting specifically Polish bank accounts.
However to give you an insight as to the impact of such malware head over to the blog post about one of the oldest popular infiltrations, the case of Operation Shady Rat which was made notable by Mcafee in 2011.









Comments
Post a Comment